Weekly review of new packages uploaded to Qubes OS repositories. Link to previous Newsletter here .
Alphabetically sorted list of new packages uploaded to Qubes OS repositories
kernel-515-5.15.186-1.qubes.fc37.x86_64.rpm
kernel-515-devel-5.15.186-1.qubes.fc37.x86_64.rpm
kernel-515-modules-5.15.186-1.qubes.fc37.x86_64.rpm
kernel-515-qubes-vm-5.15.186-1.qubes.fc37.x86_64.rpm
kernel-6.12.35-1.qubes.fc37.x86_64.rpm
kernel-6.12.35-1.qubes.fc41.x86_64.rpm
kernel-61-6.1.142-1.qubes.fc37.x86_64.rpm
kernel-61-devel-6.1.142-1.qubes.fc37.x86_64.rpm
kernel-61-modules-6.1.142-1.qubes.fc37.x86_64.rpm
kernel-61-qubes-vm-6.1.142-1.qubes.fc37.x86_64.rpm
kernel-66-6.6.95-1.qubes.fc37.x86_64.rpm
kernel-66-devel-6.6.95-1.qubes.fc37.x86_64.rpm
kernel-66-modules-6.6.95-1.qubes.fc37.x86_64.rpm
kernel-66-qubes-vm-6.6.95-1.qubes.fc37.x86_64.rpm
kernel-devel-6.12.35-1.qubes.fc37.x86_64.rpm
kernel-devel-6.12.35-1.qubes.fc41.x86_64.rpm
kernel-modules-6.12.35-1.qubes.fc37.x86_64.rpm
kernel-modules-6.12.35-1.qubes.fc41.x86_64.rpm
kernel-qubes-vm-6.12.35-1.qubes.fc37.x86_64.rpm
kernel-qubes-vm-6.12.35-1.qubes.fc41.x86_64.rpm
python3-dnf-plugins-qubes-hooks-4.3.27-1.fc40.noarch.rpm
python3-splitgpg2_1.1.7+deb12u1_amd64.deb
python3-splitgpg2_1.1.7+deb13u1_amd64.deb
python3-splitgpg2_1.1.8+deb12u1_amd64.deb
python3-splitgpg2_1.1.8+deb13u1_amd64.deb
python3-splitgpg2_1.1.8+jammy1_amd64.deb
python3-splitgpg2_1.1.8+noble1_amd64.deb
qubes-core-agent-4.3.27-1.fc40.x86_64.rpm
qubes-core-agent-4.3.27-1.fc41.x86_64.rpm
qubes-core-agent-4.3.27-1.fc42.x86_64.rpm
qubes-core-agent-caja-4.3.27-1.fc40.x86_64.rpm
qubes-core-agent-caja-4.3.27-1.fc41.x86_64.rpm
qubes-core-agent-caja-4.3.27-1.fc42.x86_64.rpm
qubes-core-agent-caja_4.3.27-1+deb12u1_amd64.deb
qubes-core-agent-caja_4.3.27-1+deb13u1_amd64.deb
qubes-core-agent-caja_4.3.27-1+jammy1_amd64.deb
qubes-core-agent-caja_4.3.27-1+noble1_amd64.deb
qubes-core-agent-dbgsym_4.3.27-1+deb12u1_amd64.deb
qubes-core-agent-dbgsym_4.3.27-1+deb13u1_amd64.deb
qubes-core-agent-dom0-updates-4.3.27-1.fc40.noarch.rpm
qubes-core-agent-dom0-updates-4.3.27-1.fc41.noarch.rpm
qubes-core-agent-dom0-updates-4.3.27-1.fc42.noarch.rpm
qubes-core-agent-dom0-updates_4.3.27-1+deb12u1_amd64.deb
qubes-core-agent-dom0-updates_4.3.27-1+deb13u1_amd64.deb
qubes-core-agent-dom0-updates_4.3.27-1+jammy1_amd64.deb
qubes-core-agent-dom0-updates_4.3.27-1+noble1_amd64.deb
qubes-core-agent-nautilus-4.3.27-1.fc40.x86_64.rpm
qubes-core-agent-nautilus-4.3.27-1.fc41.x86_64.rpm
qubes-core-agent-nautilus-4.3.27-1.fc42.x86_64.rpm
qubes-core-agent-nautilus_4.3.27-1+deb12u1_amd64.deb
qubes-core-agent-nautilus_4.3.27-1+deb13u1_amd64.deb
qubes-core-agent-nautilus_4.3.27-1+jammy1_amd64.deb
qubes-core-agent-nautilus_4.3.27-1+noble1_amd64.deb
qubes-core-agent-network-manager-4.3.27-1.fc40.noarch.rpm
qubes-core-agent-network-manager-4.3.27-1.fc41.noarch.rpm
qubes-core-agent-network-manager-4.3.27-1.fc42.noarch.rpm
qubes-core-agent-network-manager_4.3.27-1+deb12u1_amd64.deb
qubes-core-agent-network-manager_4.3.27-1+deb13u1_amd64.deb
qubes-core-agent-network-manager_4.3.27-1+jammy1_amd64.deb
qubes-core-agent-network-manager_4.3.27-1+noble1_amd64.deb
qubes-core-agent-networking-4.3.27-1.fc40.noarch.rpm
qubes-core-agent-networking-4.3.27-1.fc41.noarch.rpm
qubes-core-agent-networking-4.3.27-1.fc42.noarch.rpm
qubes-core-agent-networking_4.3.27-1+deb12u1_amd64.deb
qubes-core-agent-networking_4.3.27-1+deb13u1_amd64.deb
qubes-core-agent-networking_4.3.27-1+jammy1_amd64.deb
qubes-core-agent-networking_4.3.27-1+noble1_amd64.deb
qubes-core-agent-passwordless-root-4.3.27-1.fc40.noarch.rpm
qubes-core-agent-passwordless-root-4.3.27-1.fc41.noarch.rpm
qubes-core-agent-passwordless-root-4.3.27-1.fc42.noarch.rpm
qubes-core-agent-passwordless-root_4.3.27-1+deb12u1_amd64.deb
qubes-core-agent-passwordless-root_4.3.27-1+deb13u1_amd64.deb
qubes-core-agent-passwordless-root_4.3.27-1+jammy1_amd64.deb
qubes-core-agent-passwordless-root_4.3.27-1+noble1_amd64.deb
qubes-core-agent-selinux-4.3.27-1.fc40.noarch.rpm
qubes-core-agent-selinux-4.3.27-1.fc41.noarch.rpm
qubes-core-agent-selinux-4.3.27-1.fc42.noarch.rpm
qubes-core-agent-systemd-4.3.27-1.fc40.x86_64.rpm
qubes-core-agent-systemd-4.3.27-1.fc41.x86_64.rpm
qubes-core-agent-systemd-4.3.27-1.fc42.x86_64.rpm
qubes-core-agent-thunar-4.3.27-1.fc40.x86_64.rpm
qubes-core-agent-thunar-4.3.27-1.fc41.x86_64.rpm
qubes-core-agent-thunar-4.3.27-1.fc42.x86_64.rpm
qubes-core-agent-thunar_4.3.27-1+deb12u1_amd64.deb
qubes-core-agent-thunar_4.3.27-1+deb13u1_amd64.deb
qubes-core-agent-thunar_4.3.27-1+jammy1_amd64.deb
qubes-core-agent-thunar_4.3.27-1+noble1_amd64.deb
qubes-core-agent_4.3.27-1+deb12u1_amd64.deb
qubes-core-agent_4.3.27-1+deb13u1_amd64.deb
qubes-core-agent_4.3.27-1+jammy1_amd64.deb
qubes-core-agent_4.3.27-1+noble1_amd64.deb
qubes-core-dom0-4.3.30-1.fc41.noarch.rpm
qubes-template-debian-12-4.3.0-202507031439.noarch.rpm
qubes-template-debian-12-minimal-4.3.0-202507031439.noarch.rpm
qubes-template-fedora-42-xfce-4.3.0-202507050157.noarch.rpm
qubes-vm-caja-4.3.27-1-x86_64.pkg.tar.zst
qubes-vm-core-4.3.27-1-x86_64.pkg.tar.zst
qubes-vm-dom0-updates-4.3.27-1-x86_64.pkg.tar.zst
qubes-vm-keyring-4.3.27-1-x86_64.pkg.tar.zst
qubes-vm-nautilus-4.3.27-1-x86_64.pkg.tar.zst
qubes-vm-networking-4.3.27-1-x86_64.pkg.tar.zst
qubes-vm-passwordless-root-4.3.27-1-x86_64.pkg.tar.zst
qubes-vm-thunar-4.3.27-1-x86_64.pkg.tar.zst
split-gpg2-1.1.8-1.fc40.noarch.rpm
split-gpg2-1.1.8-1.fc41.noarch.rpm
split-gpg2-1.1.8-1.fc42.noarch.rpm
split-gpg2-dom0-1.1.8-1.fc37.noarch.rpm
split-gpg2-dom0-1.1.8-1.fc41.noarch.rpm
split-gpg2-tests-1.1.8-1.fc40.noarch.rpm
split-gpg2-tests-1.1.8-1.fc41.noarch.rpm
split-gpg2-tests-1.1.8-1.fc42.noarch.rpm
split-gpg2-tests_1.1.7+deb12u1_all.deb
split-gpg2-tests_1.1.7+deb13u1_all.deb
split-gpg2-tests_1.1.8+deb12u1_all.deb
split-gpg2-tests_1.1.8+deb13u1_all.deb
split-gpg2-tests_1.1.8+jammy1_all.deb
split-gpg2-tests_1.1.8+noble1_all.deb
split-gpg2_1.1.7+deb12u1_all.deb
split-gpg2_1.1.7+deb13u1_all.deb
split-gpg2_1.1.8+deb12u1_all.deb
split-gpg2_1.1.8+deb13u1_all.deb
split-gpg2_1.1.8+jammy1_all.deb
split-gpg2_1.1.8+noble1_all.deb
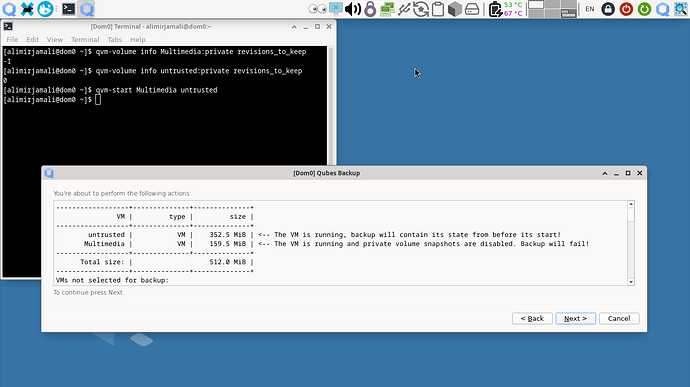
Option to disable volume snapshot and use it directly.
In addition to the usual minor fixes and patches (full list here ):
app-linux-split-gpg2 v1.1.8 (r4.3)app-linux-split-gpg2 v1.1.8 (r4.2)libnotify-bin (notify-send) is not installed.
qubes-template-fedora-42-xfce 4.3.0-202507050157 (r4.3)qubes-template-debian-12 4.3.0-202507031439 (r4.3)qubes-template-debian-12-minimal 4.3.0-202507031439 (r4.3)
core-admin v4.3.30 (r4.3)revisions_to_keep per volume to -1 to disable its snapshot and use it directly.Preloaded Disposables patches, mostly related to handling of related features and their events.qvm-pool remove.
core-agent-linux v4.3.27 (r4.3)
linux-kernel-66 (old lts) v6.6.95-1 (r4.2)linux-kernel-515 (ancient lts) v5.15.186-1 (r4.2)linux-kernel-61 (very old lts) v6.1.142-1 (r4.2)linux-kernel (lts) v6.12.35-1 (r4.3)linux-kernel (lts) v6.12.35-1 (r4.2)
Disabling of the root volume snapshot is also possible (useful for some StandaloneVMs).
By disabling qube’s private volume snapshot, user gains the following:
Any deletion from the qube’s private volume while it is running will be instantly freed up from the respective storage pool (except file driver and some weird scenarios where trim/discard is not available).
Qube start could be a little bit faster but qube shutdown could be considerably faster if there were a lot of changes to the private volume.
A little bit less wear and tear to NAND (SSD) storage.
Some performance gain.
On the other hand, user losses the option to:
Backup the qube while it is running (using the snapshot before its start).
Cloning it while it is running.
Starting a DispvM from it while it is running (in case it is a DispVM template).
17 Likes
These look like a nice feature list depending on a use case. @fiftyfourthparallel Perhaps it could be added to Quick Quality-of-Life Improvements ?
4 Likes
In practice I imagine this will be most useful for larger qubes with a lot of disk changes - some databases, some blockchain qubes, etc. I don’t think it’s that useful for “normal usage”.
5 Likes
On the contrary. I am always low on storage space and I do not want to wait to shutdown any qube to free up storage. I am one of those people who is going to set revisions_to_keep to -1 for almost all qubes
4 Likes
Contrary-contrary: Default resilience of QubesOS is a great selling point. Thanks to disposables, limited persistence, and snapshots, it grows back like mold despite all the stupid things I do.
Kind of makes one spoiled tho.
4 Likes
You currently have them set to 0, but while the VMs are running they still create a snapshot that is deleted when shutdown?
2 Likes
So, disabling snapshots at app-vm:root have no consequences except that you can’t make backup if such vm is running (so I need one vm to which a backup is saved with snaps on).
But what about private on disposable templates? Like what are the consequences of setting
qvm-volume config dvm-audio:private revisions_to_keep -1
is /rw directory kept on private volume?
is numbered disposable volume snapshoted?
$ qvm-volume config dvm-default:root revisions_to_keep 2
$ sudo lvs |grep disp7974
vm-disp7974-private-snap qubes_dom0 Vwi-aotz-- 2.00g vm-pool vm-dvm-default-private 11.04
vm-disp7974-root-snap qubes_dom0 Vwi-aotz-- 20.00g vm-pool vm-tmpl-fedora-xfce-fc41-root 36.51
vm-disp7974-volatile qubes_dom0 Vwi-aotz-- 12.00g vm-pool 0.17
$ qvm-volume config dvm-default:root revisions_to_keep 0
$ sudo lvs |grep disp7392
vm-disp7392-private-snap qubes_dom0 Vwi-aotz-- 2.00g vm-pool vm-dvm-default-private 10.08
vm-disp7392-root-snap qubes_dom0 Vwi-aotz-- 20.00g vm-pool vm-tmpl-fedora-xfce-fc41-root 36.51
vm-disp7392-volatile qubes_dom0 Vwi-aotz-- 12.00g vm-pool 0.16
disposable templates don’t do root snapshots but they do private snapshots
PS:
$ qvm-volume info dvm-default:private
pool vm-pool
vid qubes_dom0/vm-dvm-default-private
rw True
source
save_on_stop True
snap_on_start False
size 2147483648
usage 237082194
revisions_to_keep 2
ephemeral False
is_outdated False
List of available revisions (for revert):
1751491439-back
1751918165-back
2 Likes
Yes. This way it is possible to backup or clone a running qube from its snapshot. Comparing the backup dialog for a running qube with revisions_to_keep == 0" to a running qube with revisions_to_keep == -1"
3 Likes
I wouldn’t mind adding this if it doesn’t have the potential for substantial harm and if someone is willing to write a short script or instructions.
2 Likes
Do I understand correctly that the user would also not be able to revert the qubes’ volume in case something bad happens and no backup exists?
3 Likes
That is correct. There will be only one copy of the volume. But it should be noted that this option could be controlled separately for private volume and root volume.
1 Like
@alimirjamali my dom0 dnf history looks like differs from the list of packages got listed here.
My last update in the history is from July 1st, which is a bit weird, because I think I had an update recently, but maybe I remember that wrong. The new packages upgraded are:
Return-Code : Success
Releasever : 4.2
Command Line : --exclude=qubes-template-* -y upgrade
Comment :
Packages Altered:
Upgrade fwupd-qubes-dom0-1.8.17-3.fc37.noarch @qubes-dom0-cached
Upgraded fwupd-qubes-dom0-1.8.14-5.fc37.noarch @@System
Upgrade qubes-desktop-linux-manager-4.2.26-1.fc37.noarch @qubes-dom0-cached
Upgraded qubes-desktop-linux-manager-4.2.25-1.fc37.noarch @@System
Upgrade xfwm4-1000:4.16.1-5.fc37.x86_64 @qubes-dom0-cached
Upgraded xfwm4-1000:4.16.1-4.fc37.x86_64 @@System
If I go back with one more update in time, that is the 21th of June:
Upgrade python3-qubesimgconverter-4.2.20-1.fc37.x86_64 @qubes-dom0-cached
Upgraded python3-qubesimgconverter-4.2.19-1.fc37.x86_64 @@System
Upgrade qubes-artwork-4.2.4-1.fc37.noarch @qubes-dom0-cached
Upgraded qubes-artwork-4.2.3-1.fc37.noarch @@System
Upgrade qubes-artwork-anaconda-4.2.4-1.fc37.noarch @qubes-dom0-cached
Upgraded qubes-artwork-anaconda-4.2.3-1.fc37.noarch @@System
Upgrade qubes-artwork-plymouth-4.2.4-1.fc37.noarch @qubes-dom0-cached
Upgraded qubes-artwork-plymouth-4.2.3-1.fc37.noarch @@System
Upgrade qubes-core-qrexec-4.2.24-1.fc37.x86_64 @qubes-dom0-cached
Upgraded qubes-core-qrexec-4.2.23-1.fc37.x86_64 @@System
Upgrade qubes-core-qrexec-dom0-4.2.24-1.fc37.x86_64 @qubes-dom0-cached
Upgraded qubes-core-qrexec-dom0-4.2.23-1.fc37.x86_64 @@System
Upgrade qubes-core-qrexec-libs-4.2.24-1.fc37.x86_64 @qubes-dom0-cached
Upgraded qubes-core-qrexec-libs-4.2.23-1.fc37.x86_64 @@System
Upgrade qubes-desktop-linux-menu-4.2.0-1.fc37.noarch @qubes-dom0-cached
Upgraded qubes-desktop-linux-menu-1.2.1-1.fc37.noarch @@System
Upgrade qubes-gpg-split-dom0-2.0.78-1.fc37.noarch @qubes-dom0-cached
Upgraded qubes-gpg-split-dom0-2.0.77-1.fc37.noarch @@System
Upgrade qubes-kernel-vm-support-4.2.20-1.fc37.x86_64 @qubes-dom0-cached
Upgraded qubes-kernel-vm-support-4.2.19-1.fc37.x86_64 @@System
Upgrade qubes-rpm-oxide-0.2.9-1.fc37.x86_64 @qubes-dom0-cached
Upgraded qubes-rpm-oxide-0.2.8-1.fc37.x86_64 @@System
Upgrade qubes-utils-4.2.20-1.fc37.x86_64 @qubes-dom0-cached
Upgraded qubes-utils-4.2.19-1.fc37.x86_64 @@System
Upgrade qubes-utils-libs-4.2.20-1.fc37.x86_64 @qubes-dom0-cached
Upgraded qubes-utils-libs-4.2.19-1.fc37.x86_64 @@System
If I go back one more update, that is almost a month earlier, end of May. Am I missing something or this is really look weird?
1 Like
Also the last few days my Fedora VMs stopped getting any updates, that is maybe unusual but normal (as they basically push an update almost every day), but now I am wondering if that is really the case.
It appears you did not update your system before that in a very long time. The fwupd-qubes-vm-1.8.17-3 is from 8 the June. The qubes-desktop-linux-manager-4.2.25-1 is from 8th September. And there is a newer version released on 6th June. The xfwm4-4.16.1-5 is from 7th June.
Two points. 1st of all, many of the updates I post are only specific to Qubes OS r4.3 (Development Testing branch). It would take time for some of them to be backported to r4.2. And the updates I post for r4.2 is also for its testing branch. It could could take weeks or months for them to be transferred from testing branch to stable branch.
3 Likes
Thank you for the answer! That sounds scary. What could cause my dom0 not to update these packages and not see these updates? How can I make sure that everything is up to date? Also, these things sounds like a pretty big security flaw. Should I reinstall my whole OS maybe?
alimirjamali:
Two points. 1st of all, many of the updates I post are only specific to Qubes OS r4.3 (Development Testing branch). It would take time for some of them to be backported to r4.2. And the updates I post for r4.2 is also for its testing branch. It could could take weeks or months for them to be transferred from testing branch to stable branch.
I’m not sure if this is useful information, but my OS is 4.2.4.
@alimirjamali do you think this problem is connected too?
qubemanager:
Also the last few days my Fedora VMs stopped getting any updates, that is maybe unusual but normal (as they basically push an update almost every day), but now I am wondering if that is really the case.
Is there any Fedora 41 updates in the last two days? If yes, I cannot see and fetch them even if I try to update with the GUI.
No need to worry. Just update more frequently. Maybe twice a week.
it is fine. Just remember that the (4.2) updates I post here take some time to be delivered to stable stream. If you click any and follow the link on Github, you will see some labels at the right side of the page. If you see only testing labels, this means that they have not been released for general users and they need more time. For example kernel lts one is not yet released for general users.
1 Like
qubemanager:
@alimirjamali do you think this problem is connected too?
qubemanager:
Also the last few days my Fedora VMs stopped getting any updates, that is maybe unusual but normal (as they basically push an update almost every day), but now I am wondering if that is really the case.
Is there any Fedora 41 updates in the last two days? If yes, I cannot see and fetch them even if I try to update with the GUI.
I am not 100% certain. it is hard to keep track of all updates. But if there was an issue, the GUI updater should provide an error message.
Thank you @alimirjamali ! I take it easy and will do as you say.
There is something, but it is not an error message. I guess it is fine, still I copy that here just in case:
Updating fedora-41-xfce
ls: cannot access '/usr/sbin/meminfo-writer': No such file or directory
Refreshing package info
Removed 0 files, 0 directories (total of 0 B). 0 errors occurred.
Installed packages:
None
Updated packages:
None
Removed packages:
None
qubemanager:
There is something, but it is not an error message. I guess it is fine, still I copy that here just in case:
Updating fedora-41-xfce
ls: cannot access '/usr/sbin/meminfo-writer': No such file or directory
Refreshing package info
Removed 0 files, 0 directories (total of 0 B). 0 errors occurred.
Installed packages:
None
Updated packages:
None
Removed packages:
None
This is fine. Follow this thread on forum for more information:
after boot this morning (i power down each evening) I got the usual notification that fedora41 template had updates, and started the update.
fedora41 result:
[fedora41_update_error]
dom0 check:
[dom0_error]
the nature of the missing file has me concerned.
i’m very much a vanilla qubes user. i don’t mess around with the environments. i avoid installing anything outside the delivered repos.
any thoughts?
2 Likes