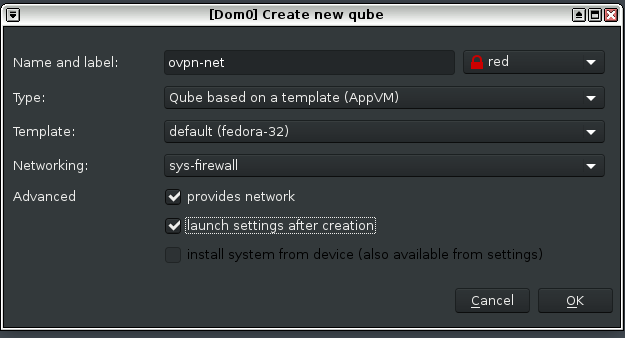
1. Create a new qube with these settings:
Type: AppVM
Template: Fedora
Networking: sys-firewall
Advanced: check “provides network” and “launch settings after creation”
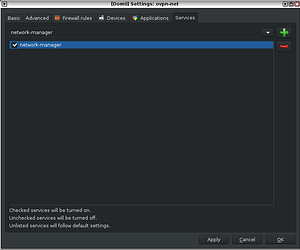
2. When the created-qube window settings showsup, go directly to tab “Services”
2.1 Select the service “network-manager” then click “+” to add the respective service
2.2 Check the “network-manager” field box then “Apply” → “OK”
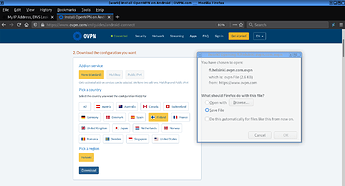
3. Download the vpn config file from ovpn website (this guide used the ‘finland’ ovpn config file)
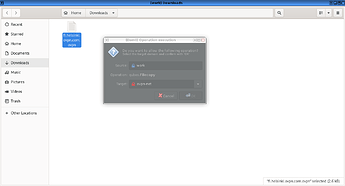
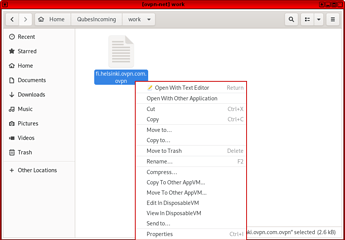
4. Use the file manager to access the folder with the downloaded ovpn-config-file
4.1 Move the file to the created-qubes-appvm
5. If you have done everything right then the created-qubes-appvm will start automatically and will receive ovpn-config-file.
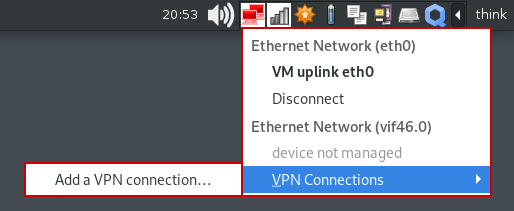
6. An ethernet network connection icon from the created-qube-appvm will show up on “notification area” after the appvm start.
6.1 Select and go to: Ethernet Network → VPN Connections → *Add a VPN connection…
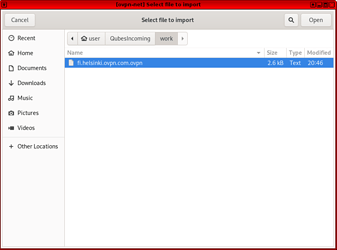
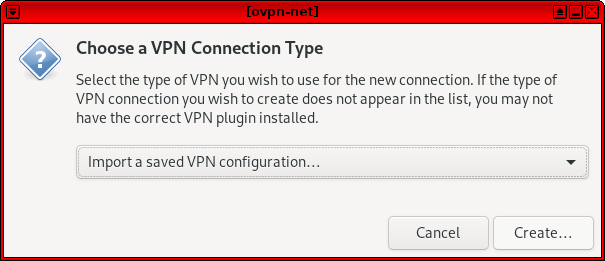
6.2 Choose “Import saved VPN configuration”
6.3 Browse to “QubesIncoming” directory and select the downloaded ovpn-config-file.
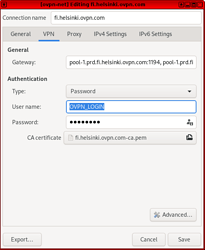
7. A window will show up with the ovpn configuration, select the “VPN” tab
7.1 On the “Authentication” field type your “ovpn login” and “password” then “SAVE”
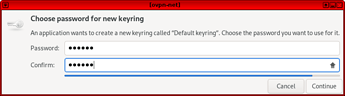
8. Choose password for keyring or leave blank
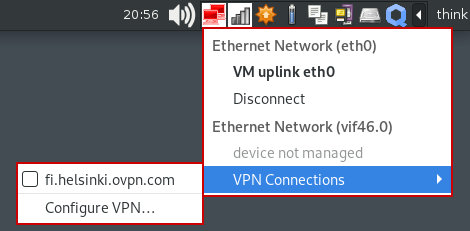
9. Connect to OVPN: Notification Area → Ethernet Network → VPN Connections → OVPN_CONFIG(fi.helsinki.ovpn.com)
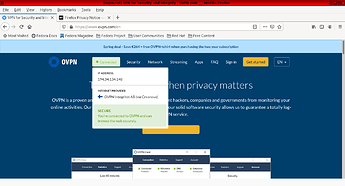
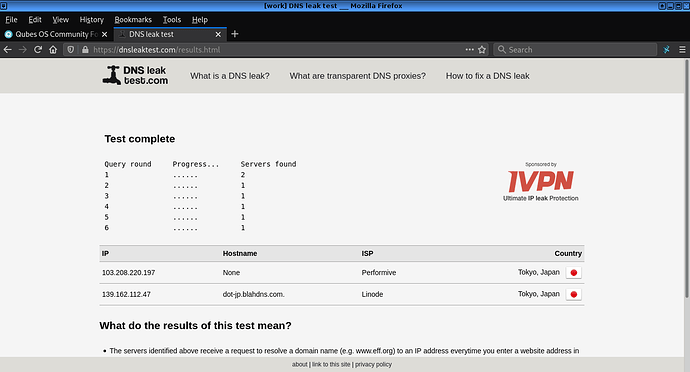
10. Check the connection using the OVPN SITE trough the top menu.
If you have done everything right then you’re browsing trough OVPN.
If your vpn connection goes down while you’re browsing you can prevent dns-leak:
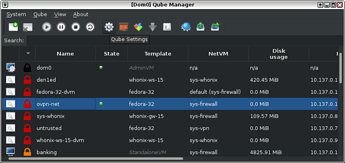
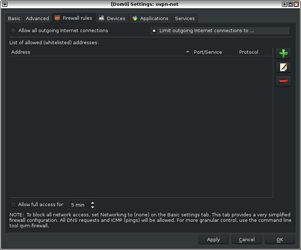
1. Open the Qube-Manager, select the created-qubes-appvm and open the qubes settings
2. Go to the “Firewall rules” TAB and select the “Limit outgoing internet connections to…” option
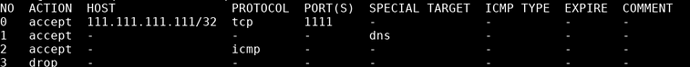
3. Click “+” then type the remote address
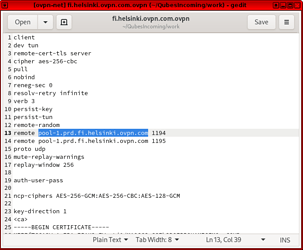
3.1 To find the correct addresss open the downloaded ovpn-config-file with text-editor
3.2 Locate the “remote” line address and copy it.
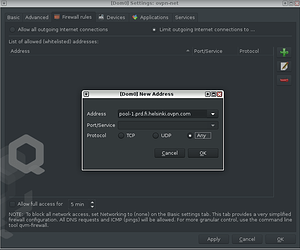
3.3 Go back to “Firewall rules” TAB, click “+” to fill in the fields with the copied address:
Address: pool-1.prd.fi.helsinki.ovpn.com(the one used in this guide is the finland ovpn-config-file)
Port/Service: Leave blank
Protocol: Any
4. Click “Apply” then “OK” and enjoy it.