I am a new user, moving from Windows 7.
The installation documentation is insufficient, there is not enough information provided for new users to understand or make deliberate choices with known/expected consequences.
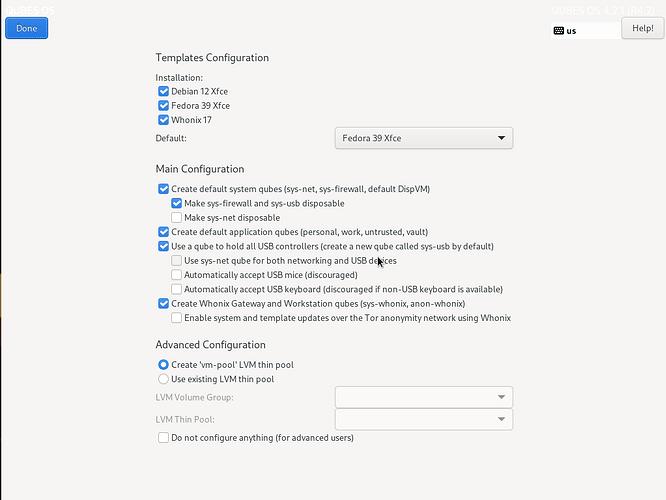
Consider this image
from Installation guide — Qubes OS Documentation.
Unfortunately, the description that follows is indeed brief, it is superficial and somewhat redundant. The information provided does not explain further what can be inferred from the user interface itself.
Consider the first description:
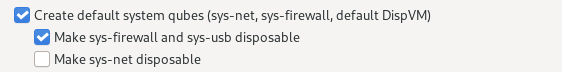
Create default system qubes: These are the core components of the system, required for things like internet access. You can opt to have some created as disposables.
There are too many questions that are not answered anywhere in the documentation:
- Why would
sys-firewallandsys-usbbe disposable, together, and not separately, assys-netis? - What are the consequences (both benefits and disadvantages) for each of these services being or not disposable? (please let’s not waste our time with the definition of disposable, and no, a link to the disposable general documentation does not answer this question)
- How can the result of each of the possible child options (regarding these services being disposable) be recreated/altered, manually, after the installation? (and thus, demonstrating to the user that if they change their mind, they don’t need to reinstall from scratch to try out something different)
- What are the consequences (both benefits and disadvantages) for each of these services being or not created? (the parent checkbox checked, or not)
- How do their consequences interact with each other?
- How can each of these services be created manually, after the installation?
Answering these questions here does not help. The documentation should be updated instead. In fact, probably most of the information replied in this forum should be migrated in the documentation. The number of threads, and how often certain subjects reappear in different guises, these are demonstrations of how much the documentation itself should be improved.