Thank you @deeplow @adw @Plexus and @unman for your responses. If I am the only one known to have faced such a recurrent problem (while using a standard recent Lenovo Thinkpad), I admit that this is worrying. Also, I didn’t move to Qubes OS without a reason. Should an attacker be exploiting a zero-day in Qubes, I think he would have been able to steal from the vault gpg key, keepass database, as well as log-in credentials in the internet-connected VMs, while at the same time rendering my OS unusable. This means that the attacker would have achieve his purposes, and that Qubes’ security did not foil an attack but was solid enough to expose that something went wrong.
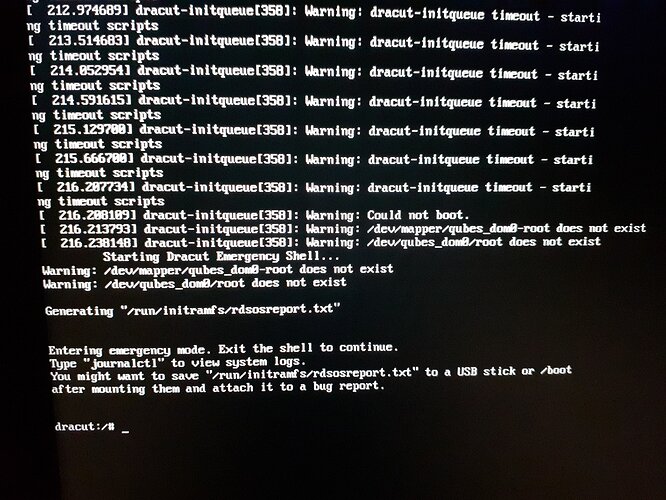
On a related issue, just to explain how difficult my journey with Qubes has been (and still is), in 2019, I faced a different albeit equally recurrent (every few weeks) major malfunction in Qubes that seemingly very few if anyone had. Back then, Qubes recurrently, without reason, boot into this screen:
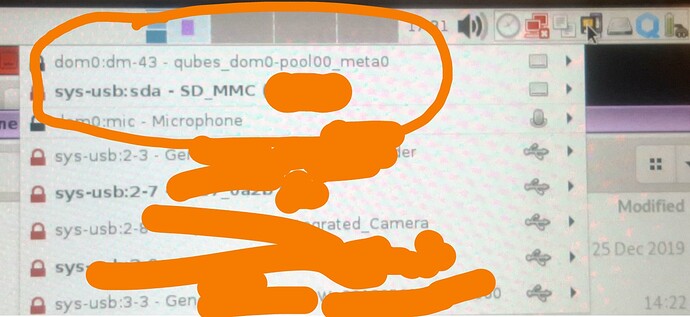
I searched online using the words in front of me, and found “somewhere” instructions that did get Qubes operational again. HOWEVER, when Qubes booted again, I saw this new Dom0 piece of information in the Qubes Devices:
So I had to re-install Qubes as I could not consider this to be safe.
I’m reinstalling Qubes every few months because it’s failing. It’s failing not because something is wrong with Qubes, because I’m the only one having these problems. But because…?
And should such a problem happen again, is there a way for the Qubes team to examine my laptop and understand what happened, just in case they need to fix something in Qubes?