That might be true and that might all be nothing and perfectly secure, however some thought process and acknowledgement of this being an issue would be appropriate.
However, on Introduction to Trusted Execution Environment: ARM's TrustZone - Quarkslab's blog I would the following image:
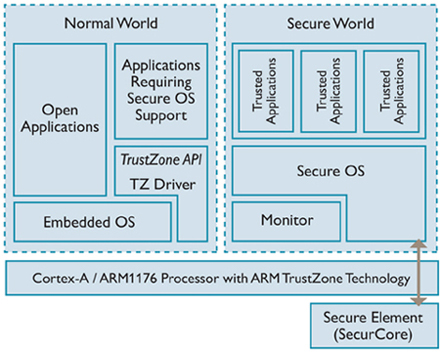
You can see there is,
- A) the Embedded OS, and
- B) the Secure OS.
The question arises, what runs by default in the TEE? Nothing? If so, that’s great. But did anyone check?
Quote:
Vulnerabilities in TrustZone itself
…
On the other hand, the development of an entire operating system is a daunting task that often involves many bugs. Operating systems running TrustZone are no exception to the rule. A development error leading to memory corruption in the Secure World kernel causes total system corruption in Secure World, making its security obsolete. It also totally compromises the Normal World which is accessible from the Secure World.
Finally, compromising the TEE OS can be done before it is even executed if a vulnerability is found in the secure boot chain, as has been the case several times
It also seems to be that TrustZone a really nice place for malware to persist even after a complete re-installation of the “normal” (non-TrustZone) operating system.
It might still be fine. I am just saying, this certainly warrants acknowledgement, research, consideration. Completely ignoring the topic of TrustZone seems wrong.