Soon:
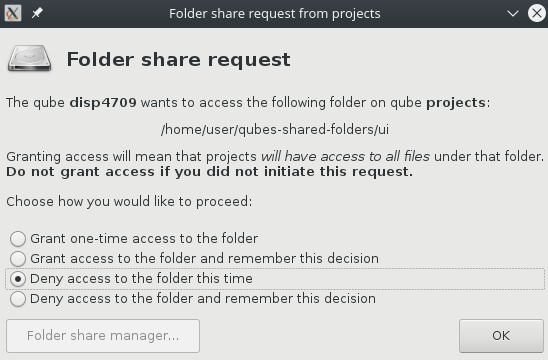
See thread Design questions for the next steps of the Qubes shared folders service - #2 by Rudd-O
This code needs testers and reviewers!
Soon:

See thread Design questions for the next steps of the Qubes shared folders service - #2 by Rudd-O
This code needs testers and reviewers!