In fact, do I understand your method correctly? Your method is to install Gnome Software in template, make it able to install flatpak apps in template, and then you add flatpak app that you need in “applications” menu of app qube as it is usually done with regular apps?
Then you don’t need to go through all this hassle, you can install a program in an AppVM in your user directory. This way, you don’t have to do it in the template and the setup is simplified.
flatpak remote-add --user --if-not-exists flathub https://dl.flathub.org/repo/flathub.flatpakrepo
flatpak install --user org.telegram.desktop
That’s all you need. You can click on “Sync menus” in the qube settings, Applications tab to have telegram available in the menu.
It seems I wasn’t consistent with my examples. The IP doesn’t matter as long as it’s not a working default route. There is now may 127.0.0.1 or 127.0.0.2 are a default route ever.
My big thank you. Have read about how flarpak is working and almost fell asleep. As I understand flatpak app already runs sandboxed and you don’t need to perform any additional actions for that, right? The only thing that is interesting for me now is how to look what hardware permissions has flatpak app. While googled, stumbled across such application as Flatseal, made for configuring permissions that app has. Can it be installed in an app qube the same way as you shown me for Telegram? Will it (Flatseal) actually work there?
As for the desired command I found --nodevice=all to restrict access for all devices but not sure if it’s what I need. I want ability to see what hardware permissions Telegram flatpak has and to cancel these permissions if there are any. I suppose it should not break the work of app. Correct me if I’m wrong.
You can see on flathub what sandboxing is done for each program. Sometimes it’s good, sometimes it’s reallyyy loose.
You can also check if the packager was certified to be the original team behind the project, if it’s not the case, you can have trust issue for that program. For instance, Firefox flatpak is handled by people doing Firefox so it’s fine, but for Steam it’s done by a third party.
There is said that it has access to some “runtime subfolder pipewire-0”. Made a little search and seems it means access to devices as camera, sound server (don’t know what kind of server this is), screencast. What does it mean in context of Qubes? Especially in context of app qube. How dangerous would be these permissions in app qube?
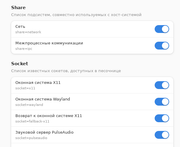
Anyway, I installed Flatseal and looked what permissions Telegram has. Here’s what:
About this screenshot I’m interested in what is share=ipc (it is named “interprocess communications” if to translate using online translator). Whether should I turn it off or leave as is.
UPD: Googled. It really didn’t clear for me much but one thing that I understood is that this way it probably can find out much about my system (at least about processor), so I probably disable it.
About sockets would you suggest to disable something? I think I can disable PulseAudio safely. I don’t need sound notifications (and sound at all).
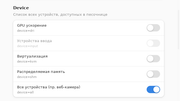
But what is most interesting for me is the section Devices. There is device=all enabled. I would like to disable it but have understanding that I probably should to enable something from that list instead. Otherwise Telegram probably cannot work (at least properly). I would enable device=input since I suspect it’s about Telegram be able to see keyboard but it can’t be enabled even when device=all is disabled. It says that installed Flatseal version doesn’t support that. But if Telegram will still see keyboard without this parameter, should I enable something else from Device list? Maybe device=kvm (this parameter named “Virtualization”).
UPD: To clarify for you since you don’t understand Russian. Here’s what in that section written:
GPU acceleration: device=dri
Input Devices: device=input
Virtualization: device=kvm
Shared Memory: device=shm
All Devices (e.g. webcam): device=all
Taken from here.
PS. Flatpak.org docs are offline now so I even can’t look what those parameters mean. ![]()
I think you can just not care about devices as Qubes OS already separate everything. As long as you don’t include a webcam into the qube, it won’t have access to a webcam, there are no GPU acceleration either and virtualization is a no-go due to Xen.
Some programs actually need some permissions to work, what Telegram requires seems quite legit to me.
Tried Telegram and found myself not able to find where its tdata is located (I edited connection settings, so there sure already should have appear tdata folder). Of course its usual location .local/share/ hasn’t it now. Looked into all folders related to flatpak (by finding folders called flatpak) and not found it yet. Could you suggest where I could look else? Googled but there was no such topic yet.
Every flatpak program is prefixed with /home/user/.var/org.something.name/ then you will have a config directory that represents the usual .config and data that is .local/share/
Flatpak programs don’t mix their settings with your home directory, and it’s nice ![]()
Thanks, I already found. ![]()
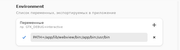
Do you happen to know what these parameters are? I’m thinking now whether to delete these paths or to leave. Want to make the app as hardened as possible. Googled about first screen. It’s some kind of debugging thing (if it’s actually somehow related to this path). But my understanding of the material is not sufficient to draw a definitive conclusion as to how big a potential threat it can be. This path is entitled “variables”
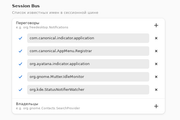
And this section entitled “negotiation” (and has an explanation “list of known names in the session bus”). Don’t know if it’s correct translation for this technical parameter. But there are no other variants of translation that could contain other meanings.
I think you are overthinking this. This is not because they is a list of permissions that it’s possible to reduce it. The team packaging the software already certainly reduced down to the most possible.
flatseal is more useful to ADD permissions ![]() (or inspect the current config).
(or inspect the current config).
I searched more about share=ipc and there often proc/ directory was mentioned. Could it be the way how Telegram app could see my processor info? Is there actually any way how to prevent flatpak application from seeing any information about my processor? Maybe exactly this is the reason to disable share=ipc function?
…but consider this:
Not sure what to think. Micah Lee is very knowledgeable but the criticisms of Flatpak also seem legit.
It’s outdated by now, and it never really was that legit of an article. Bubblewrap has always been a sound sandboxing technology, and Flatpak itself has improved significantly over the past 6 years. Hari Rana wrote a response to Flatkill’s claims in late 2021, which highlights the hyperbole used in the article.
There’s also this article, which raised more security considerations, but like Flatkill, it too was based on hyperbole and a misunderstanding of Flatpak’s technologies, and its claims were debunked shortly thereafter.
Bubblewrap (and other container technologies) will probably never be as secure as full virtualisation, but Flatpak’s implementation of it is better than nothing.
OK, maybe you can’t say how it works with processor info, but at least I will not break something in the flatpak principle of working if I disable that (share=ipc) parameter?
Just recently realized that I don’t know yet how to update flatpaks in my case. What command should I use for this?
flatpak upgrade