qvm-create --template fedora-34 --label red sys-usb
DONE...but why does it make it a a regular qubes and not a service? like service: firewall or service: sys-net
qvm-prefs sys-usb virt_mode hvm
ERROR..... qvm-prefs: error: unrecognized arguments: hvm
THats as far as I got tonightI deleted this ( qube: sys-usb)
Don’t understand why it makes it a regular qube template and not a service.
That’s just a UI thing and it would have shown as a service would you have followed all my steps.
That worries me a big deal. Are you sure there where no typos? Can you tell me the exact CPU you are using? Does it have IOMMU / Vt-d?
Yes those features are in BIOS and I have them enabled .
Both CPUs are
2678-v3 haswell
It is from this family of CPU’s
Upon researching there isn’t much you will find. When digging deeper in Intel they actually state these are special processors and not much info is available.
To answer how I came across this beast was at a bank auction. Normally these type of servers are destroyed. But being the situation we are in at the moment places are closing up and they (financial and health) industries are trying to reclaim there loses.
Now as for the 4 hot swappable bays. I was told they where used to record activity that happened on the server and changed out regularly. Think of tape drives they said.
The hot swappable flexbay nvme was the key/token used to access the server…
That’s all they told me
One more thing how do I know for a fact those are my processors.
I Tor this beast down and cleaned it. Upon re-thermaling the cpus (2) I researched the numbers stamped on the dies.
Yes I have… (2) 2678-v3 hadwells on this beast!!
Good night everyone, hope to get this sys-usb working.
As for Qubes 4.1 running?
Extremely fast & smooth, i really can’t believe it
This animal is loaded
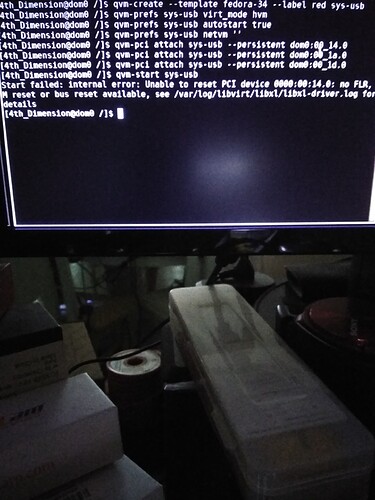
@sven…Good morning, yes there was a “typo’” so I was able to do the first set of cmds you have me and it work up till this error…
So stuck using PS/2 and my mouse is buggy
For others who do not look at pictures, the error message happened at qvm-start sys-usb and reads Start failed: internal error: Unable to reset PCI device ...
@B_ryr we are VERY close to have it working. In fact the error you see is the one I anticipated and already gave you the solution to in my original post:
qvm-pci detach sys-usb dom0:00_14.0
qvm-pci detach sys-usb dom0:00_1a.0
qvm-pci detach sys-usb dom0:00_1d.0
qvm-pci attach sys-usb --persistent --option no-strict-reset=true dom0:00_14.0
qvm-pci attach sys-usb --persistent --option no-strict-reset=true dom0:00_1a.0
qvm-pci attach sys-usb --persistent --option no-strict-reset=true dom0:00_1d.0
qvm-start sys-usb
Once we confirmed it working, you probably want to add the dom0 kernel parameter to ignore USB devices during startup for security reasons. You would enter your password with the PS/2 keyboard and once the sys-usb starts the USB keyboard and mouse start working.
@Sven
This is AWESOME!!
So I will leave the “sys-usb” it created and then do your next cmd’s tonight when I get home from work… And let you know.
As for this… “Once we confirmed it working, you probably want to add the dom0 kernel parameter to ignore USB devices during startup for security reasons.”
I don’t understand how to do this, could you please teach/show me how to accomplish this. As YES it would be very important to me to have
“ignore USB devices during startup for security reasons.”
Since you do have a PS/2 keyboard, I will skip the usual warnings here and just advise that you wait with this until you have verified that your sys-usb is working now.
- Open the file
/etc/default/grubin dom0. - Find the line that begins with
GRUB_CMDLINE_LINUX. - Add
rd.qubes.hide_all_usbto that line. - Save and close the file.
- Run the command
grub2-mkconfig -o /boot/grub2/grub.cfg(legacy boot) orgrub2-mkconfig -o /boot/efi/EFI/qubes/grub.cfg(EFI) in dom0. - Reboot.
The command line way of creating sys-usb is the same as the GUI way outlined in the documentation. Doing it on the command line is simply easier when instructing / helping through a text based medium like this one here.
@Sven
It WORKED!!!
But it still shows as
Qubes: sys-usb
and not as
service: sys-usb
like
service:firewall or service: sya-net.
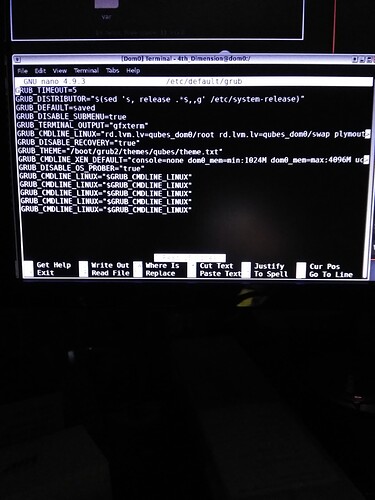
Ok, I found what you want me to edit…
But how and where in this line…
GRUB_CMDLINE_LINUX="rd.lvm.lv=qubes_dom0/root rd.lvm.lv=qubes_dom0/swap plymout>
OK, after rebooting “sys-usb” is working 100%, mouse and keyboard, all USB external drives are where they need to be in “sys-usb”
Just these 2 issues
-sys-usb still shows as a (qube: sys-usb) not a service:
- for whatever reason every time I log in now and get to time qubes desktop. Terminal and file manager are open. LIke where I left off.
Why? Is something cached, can it be cleared?
Do you see the 5 lines at the end, all containing GRUB_CMDLINE_LINUX="$GRUB_CMDLINE_LINUX"? I am pretty sure they are from your 5 attempts at running the salt recipe and failing somehow. In any case, you can remove all 5 of them as they are not doing anything and replace them with this one line:
GRUB_CMDLINE_LINUX="$GRUB_CMDLINE_LINUX rd.qubes.hide_all_usb"
Mine shows as a qube too and you are not the first to find this confusing. It’s a thing only the menu does. Neither the Qube Manager GUI nor the qvm-ls command line will make such a distinction. @ninavizz maybe this is confusing more then it helps?
The basis of whether a qube is shown as a ‘service’ or not is whether its provides_network property is true or false. In other words: what we commonly call ‘proxy qubes’ (qubes that can be selected as ‘netvm’ for another qube) are shown as ‘service’ in the menu.
Unless you want your sys-usb to provide network to other qubes (e.g. USB-based tethering of a phone hotspot) or you just “need” it to say ‘service’ in the menu, it makes little sense for sys-usb to provide network.
That’s an XFCE thing. Either you checked the ‘Automatically save session on logout’ option in the Settings app, or you need to go to the ‘Saved Sessions’ tab also under ‘Session and Startup’ and hit the ‘Clear Saved Session’ button.
@Sven
Yes I was trying to figure out what the hell was going on for my "sys-usb and why I couldn’t create it, so that’s why I posted…
ok I’ll remove those 5 lines and add that one you have stated…
GRUB_CMDLINE_LINUX="$GRUB_CMDLINE_LINUX rd.qubes.hide_all_usb"
As for sys-usb, I understand now about (qube vs service) your explanation cleared it up.
I may have check something in xfce and will clear…‘Session and Startup’
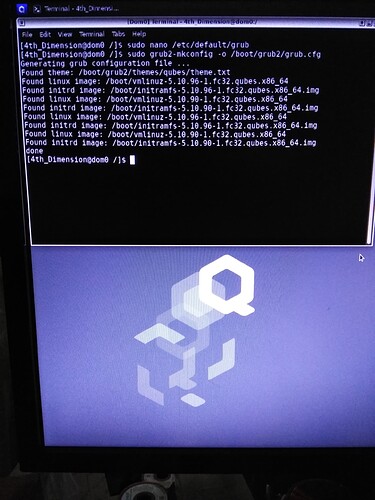
Now for making the grub…is this correct??
user@dom0 /] sudo grub2-mkconfig -o /boot/grub2/grub.cfg
Now for making the grub…is this correct??
As outlined in the documentation, there is grub2-mkconfig -o /boot/grub2/grub.cfg for legacy boot and grub2-mkconfig -o /boot/efi/EFI/qubes/grub.cfg for EFI. If you are not sure which, start with the line for legacy boot and see if it worked (as in the USB devices no longer show up in dom0 when sys-usb is shutdown).
@Sven
Done!!!
sys-usb is firing off now
Also cleared my sessions in xfce
Now in the process of setting up all my internal nvme’s and other SSD’s and building out…
What a enlightening and rewarding experience this has been Sven. Thank you so much for your time,help and effort!!
This BEAST is a GO for qubes OS 4.1!!!
I will be sending you all need Intel you have requested via back channels.
I don’t have sys-usb and I use usb keyboard and mouse. I want to create sys-usb because sometimes the system lags and i think it’s because of mouse and keyboard problem. My system doesn’t have PS2 ports to test.
I want to create sys-usb but i’m afraid i will be locked out of system.
@dom0 Desktop]$ qvm-pci | grep USB
dom0:01_00.0 USB controller: Advanced Micro Devices, Inc. [AMD]
dom0:08_00.0 USB controller: ASMedia Technology Inc. ASM2142 USB 3.1 Host Controller
dom0:09_00.2 USB controller: NVIDIA Corporation TU106 USB 3.1 Host Controller
dom0:09_00.3 Unknown: NVIDIA Corporation TU106 USB Type-C UCSI Controller
dom0:0c_00.3 USB controller: Advanced Micro Devices, Inc. [AMD] Matisse USB 3.0 Host Controller
@dom0 Desktop]$ qvm-ls | grep usb
USB-HDD Halted AppVM red tpl-deb-11-sys-usb -
tpl-deb-11-sys-usb Halted TemplateVM black - -
dom0 Desktop]$ qvm-ls | grep TemplateVM
debian-11 Halted TemplateVM black - -
fedora-34 Halted TemplateVM black - -
fedora-34-minimal Halted TemplateVM black - -
kali Halted TemplateVM black - -
kicksecure-16 Halted TemplateVM red - -
tpl-deb-11-android Halted TemplateVM black - -
tpl-deb-11-audio Halted TemplateVM black - -
tpl-deb-11-browser Halted TemplateVM black - -
tpl-deb-11-mail Halted TemplateVM black - -
tpl-deb-11-min Halted TemplateVM black - -
tpl-deb-11-office Halted TemplateVM black - -
tpl-deb-11-signal Halted TemplateVM black - -
tpl-deb-11-sys-firewall Halted TemplateVM black - -
tpl-deb-11-sys-mgmt Halted TemplateVM black - -
tpl-deb-11-sys-net Halted TemplateVM black - -
tpl-deb-11-sys-usb Halted TemplateVM black - -
tpl-deb-11-vault Halted TemplateVM black - -
tpl-fed-34-printer Halted TemplateVM black - sys-firewall
whonix-gw-16 Halted TemplateVM black - -
whonix-ws-16 Halted TemplateVM black - -
cat /etc/default/grub | grep hide_all_usb is blank.
I want to create sys-usb to restart the App when it lags or to trouble shoot more about what’s causing the issue. currently i’m not using any sys-usb.
Thank you for any suggestions.