Hi,
I’d like to point out right away that this tutorial is not mine - I received it in the mail and thought it would also be useful for members of the Qubes community.
Summary: nfttables w Qubes 4.2:
- [4.2 changelog]: DomU firewalls have completely switched to nftables. (#5031, #6062)
-
@Sven : Firewall works differently in R4.2. You are using a pre-release version. Instructions that worked with R4.1 will no longer work with R4.2.
- Qubes OS 4.2 nftables / nft firewall guide
@Sven : Firewall works differently in R4.2. You are using a pre-release version. Instructions that worked with R4.1 will no longer work with R4.2.
1. Introduction
The article comes from this site.
Nftables appeared in version 3.13 of the Linux kernel, which was released in January 2014. Like UFW and firewalld, nftables is used to configure a firewall. It is the most difficult to configure firewall of all the previously mentioned, so using it is recommended for those with Linux experience (and angelic patience).
2. Installing
Nftables should be installed by default in most Linux distributions. However, if it is not installed, you can use the command:
sudo apt install nftables
Nftables are managed via the nft command. To view the instruction associated with this command, type man nft in the console. It is worth noting that the provided instruction is quite extensive - it has almost 4000 lines.
3. Why choose nftables?
Nftables is based primarily on configuration files (*.conf), which can be created through commands using nft. You can define many rules described in tables, which are based on protocols.
The possible families (protocol-related options) are as follows:
- ip - intended for IP version 4,
- ipv6 - intended for IP version 6,
- inet - intended for IP versions 4 and 6,
- arp - intended for ARP,
- bridge - intended for connections using a bridge.
Nftables also has three types of chain. They are:
- filter - a chain intended for packet filtering,
- nat - a chain intended for NAT, or address translation,
- route - a chain intended for routing packets.
We can also specify the range of packets to which the rules apply as follows:
From @solene:
Pro tip: When experimenting with firewall rules, here is a practical method:
- run
nft list ruleset | tee original_ruleset | tee new_ruleset- add
flush rulesetat the top of both file, that will clear all the rules before loading the new rules- make changes to
new_rulesetfor your experimentations- load the new ruleset with
nft --file new_ruleset- rollback with
nft --file original_rulesetwhen you want to revert all changes(if you do that on a remote server using ssh, make sure to not lock you out, you may want to run
sleep 3600 && nft flush rulesetto disable all rules after 1h if you don’t stop the timer, or load the original rulesetinstead of flushing everything temporarily)
4. Relatedness and differences with iptables - syntax
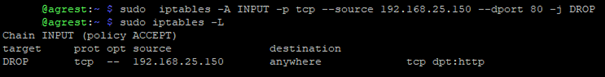
Nftables has a different syntax from iptables, but the commands can be translated from iptables to nftables quite simply. If we want to use a command from iptables in nftables, we can use the iptables-nft command. For example - we want to block traffic on port 80 for packets that come from the address 192.168.25.150.
The command in iptables will look as follows:
sudo iptables -A INPUT -p tcp --source 192.168.25.150 --dport 80 -j DROP
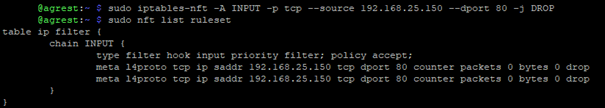
To add them to nftables, use the command:
sudo iptables-nft -A INPUT -p tcp --source 192.168.25.150 --dport 80 -j DROP
5. [4.2] configuring nftables in Qubes
Qubes OS 4.2 nftables / nft firewall guide by @solene
6. Useful commands - quick sheet
ArchLinux Wiki has a fairly simple and easy-to-read guide related to the nftables command, which is available here
nft list ruleset - Displays the current set of rules
nft flush ruleset - Removing rules, may leave device without working firewall
nft list tables - Displays the currently defined tables in the system
nft add table [family name] [table name] - Creates a table for a given family (options - ip, arp, etc.) with a given name
7. Summary
Nftables is quite a complex tool and it is no mean feat to describe its functionalities in a short article. That’s why I encourage you to test different nftables configurations in a controlled environment in order to get most familiar with the tool. The fact that it is quite easy to translate rules from iptables may help many people to “switch” to nftables.
Additional valuable learning resource nftables
-
Gentoo Linux Wiki contains some practical examples of nftables configuration.
-
ArchLinux Wiki has a fairly simple and easy-to-read guide related to the nftables command, which is available here