@unman I redid the install with just the Debian template-11 to reproduce that issue I thought linked to Downloading some dom0 packages with Debian-based updatevm fails · Issue #5233 · QubesOS/qubes-issues · GitHub. This time I used the verbose install and activated serial console on dom0 commandline, This possibly introduced more variation on the install, notably I had to use the text installer UI, which proposed different choices for partitionning (could not find how to delete the partitions from the previous install (the one that failed to download the fedora template), but I could reuse/reformat them.
The result has different issues:
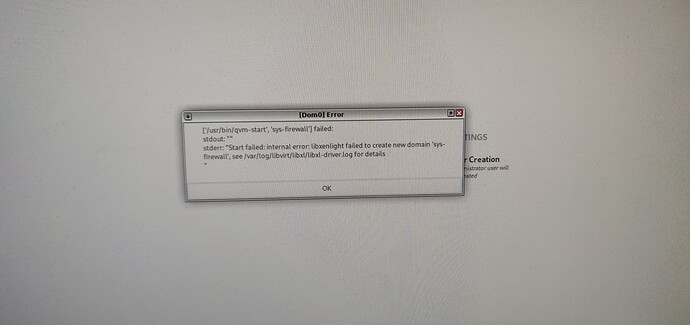
- after firstboot config I get a popup telling me sys-firewall failed to start and directs me to libxl log;
- I have no other choice than ack this and login
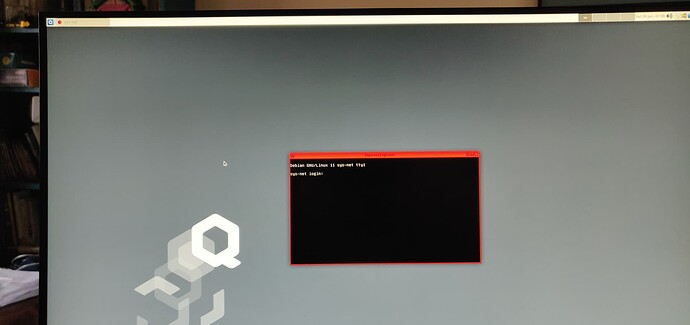
- there once logged in I get a sys-net terminal with a login prompt (!):
- a look at libxl log shows “unable to add vif devices”
Then I have a quick look around to better understand the situation, and notice that:
- no qube has anything in their appmenu
- the appmenu config GUI shows no available app in debian-11
-
qvm-sync-appmenus debian-11fails withError getting application list, can’t see anything in/var/log/qubes/*debina-11.log -
qvm-run debian-11 xtermhowever launched fine - but then when I rerun
qvm-sync-appmenus debian-11, with-vvvto be sure to have details to give, then it finally does its job (but I had done a break and was not sure of its impact) - trying to do the same with
debian-11-dvmI get a similar behaviour – namely, with some details and no break in between:- a first
qvm-sync-appmenus -vvv debian-11-dvmreminds me it needs the qube started - a second one after
qvm-startgets me the same exception (and this triggers the launch ofsys-firewall, which does succeed this time -
qvm-run debian-11-dvm xtermthis time does not work:command failed with code: 1 - and a third
qvm-sync-appmenuscall this time succeeds (though it apparently does very little, but then it’s not a template)
- a first
- I realized by chance that several qubes don’t have the same idea of what the default
default_dispvmis:sys-firewallseems to be the only one with the good idea (D debian-11-dvm) while all others showD None - I cannot access the appmenu edition for
sys-firewallin Qube Manager (greyed out) and have nothing in the appmenu, I have to useqvm-runto get any app
All in all, it looks like there is some sort of race condition, that possibly only show up because this is a low-spec machine.
Now for my initial problem with sys-gui-gpu setup:
- first manually create a partition to get all my diskspace and add it to the
qubes_dom0VG - restart the disposable
sys-firewallto clean things up after byqubes-dom0-updatetest - follow How to enable the (new) GUI VM? - #3 by marmarek
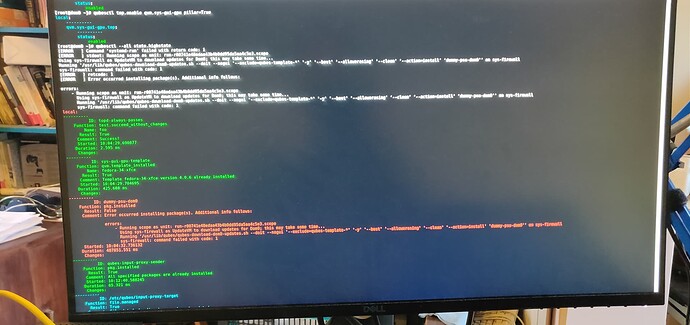
-
dummy-psu-dom0installation fails… but the/var/lib/qubes/dom0-updates/subdirectories are indeed present then insys-firewall
How do you propose we make progress here ?