That sounds scary if anything managed to reach dom0
@barto I have found at least 1 use case where a journalist may utilize QubesOS off-site remotely in a cloud (albeit not to store important stuff, but to open questionable files received). Check it out I made a question about it,
https://forum.qubes-os.org/t/qubeos-as-a-remote-cloud-virtual-thin-client/25287
… as I think it will be a safe way to not just access my compromised Google account(s) again but also open up 1 known malicious PDF which not only I need to keep as evidence but is also an important PDF I need to print as it is an LLC document (so I can report the case to other agencies and have the LLC shutdown and EIN officially ended — I currently cannot do this without re-infecting my system which I don’t have $ to trash more equipment but this method is a way to not have to have a burner or one use-case machine that will end up being thrown away which in my situation is needed as I have no $ currently)
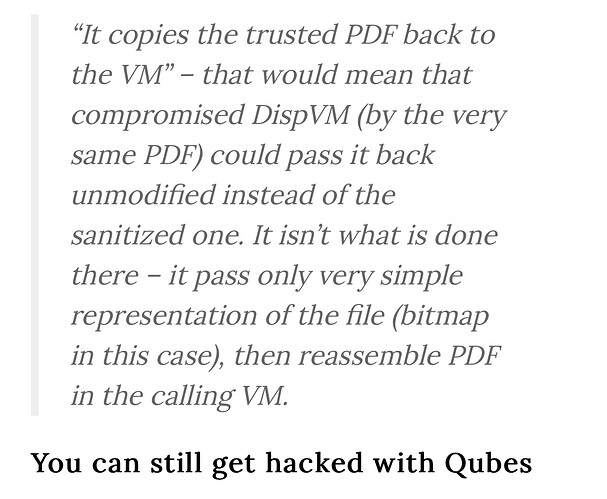
I looked into above and beyond methods and found out that opening up a PDF in a disposable is NOT full proof:
— image description start —
Screenshot of the following source:
— image description end –
Which then lead me to my new idea of possibly utilizing a “Thin Client” once I read a so-calles “off-topic” reply that lead me to Authentic8
![]()
@qubist IMHO it is NOT “off topic” and besides this thread has it in its topic …