If you were to make your way to the nealr Substack you’d find an article entitled What Hunts You? No hot link, since this is the paranoia zone, you’ll have to navigate there on your own  If you don’t understand who your adversaries are, you can’t begin to defend yourself.
If you don’t understand who your adversaries are, you can’t begin to defend yourself.
Some bona fides, with the intent that my followup questions have some weight to them.
I provided the startup environment for and later quit Project VIGILANT over the handling of the Chelsea Manning case.
If you want to see the white paper that now Senator Jonathan Ossoff circulated on Capitol Hill regarding the need for hearings on HBGary’s infowar schemes against the American people, as the original author, I’ve got a copy of it handy.
I can round up receipts on the protection of Marine Corps whistleblower Franz Gayl, as well as the ones where CIA whistleblower John Kiriakou didn’t get sent back to prison, because someone knew where to send him to get a job. Anything else I’ve done in this area was anonymous.
The origins of the January 6th Capitol Siege were with the Council for National Policy. They had an effort called Groundswell back in 2013, that got bowled over thanks to a series of articles in Mother Jones. Not my work, but I’ve become the publicly known keeper of the original documents, if you’d care to see them.
Some other stuff has happened in the ten years since then. Ask your friends in the neighborhood about me.
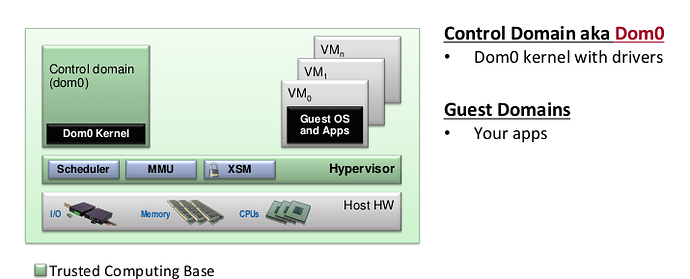
That being said, I am struggling to see how a binary blob in dom0 is going to turn into a problem for any journalists I may know, or Ukraine supporters who legitimately need to worry about FSB/GRU/SVR, or researchers in the Arab world, or civil society activists facing cartel violence.
If you read military briefings (which I do) there’s always a “So what?” at the end, sometimes it’s even that explicit. All I’ve seen thus far are theoretical concerns with huge gaps in the execution chain that would be required for this to be an actual concern.
Step by step, how does the binary blob bite someone doing work that would draw a “by any means necessary” response from a nation state?