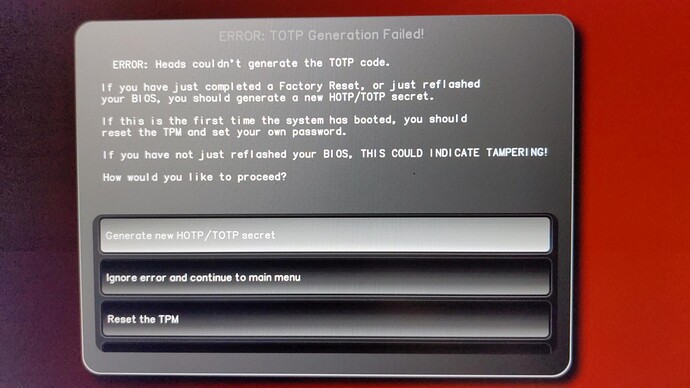
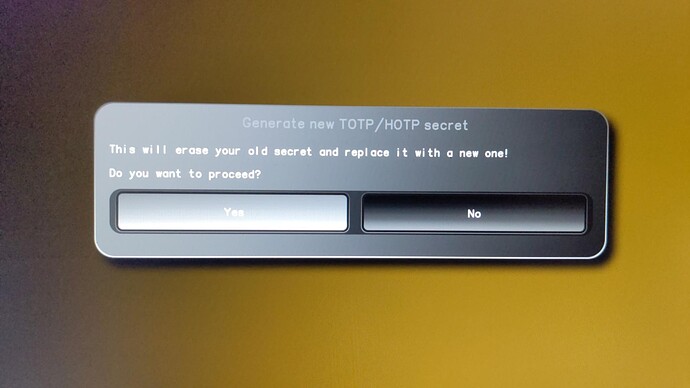
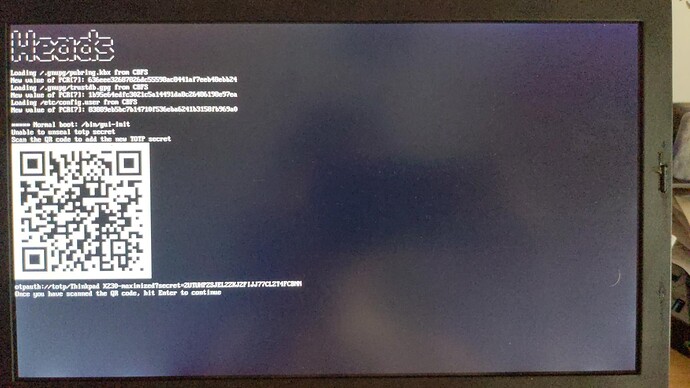
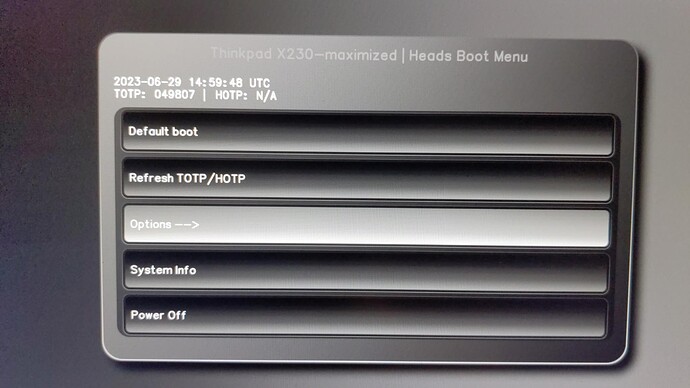
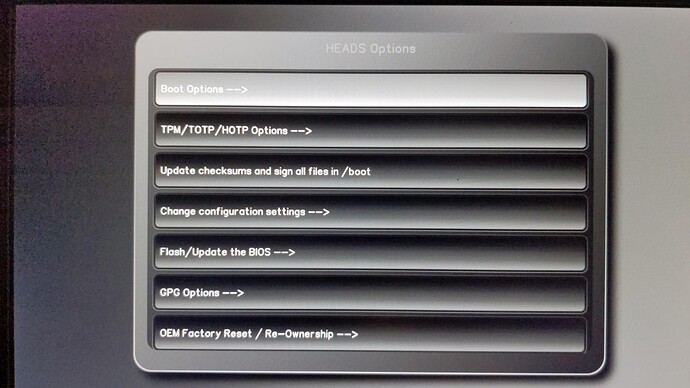
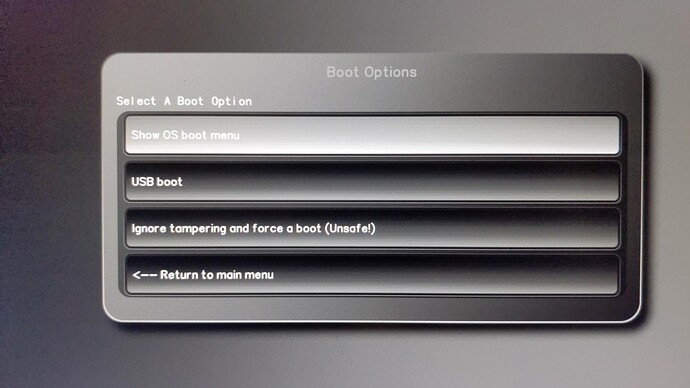
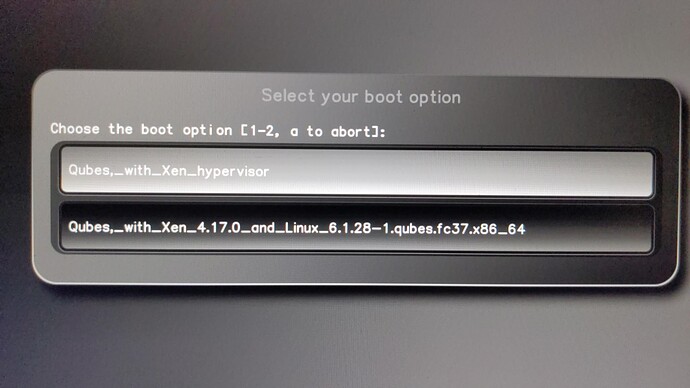
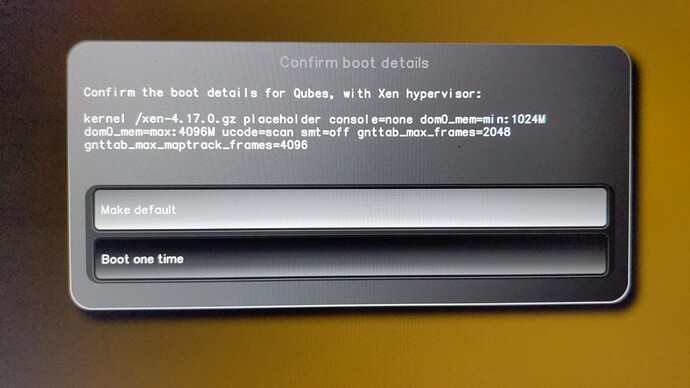
And… This is another time for board owners to willingly test and report success/failure, for those of you having external programmers.
The current PR needing testing:
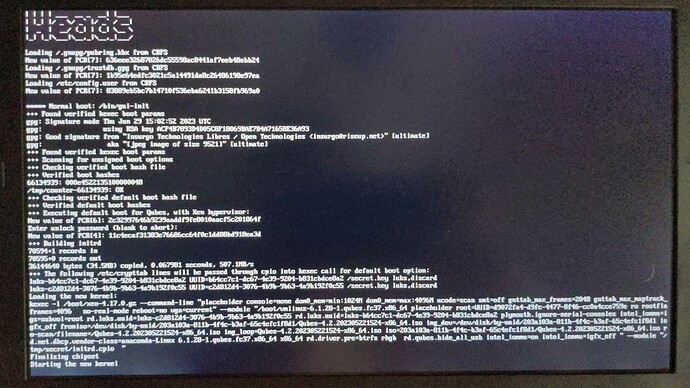
- Improves boot speed by 3 seconds (bringing x230 to under 6 seconds with a beautiful bootsplash coming from coreboot native ram initialization)
- Is the result of important collaboration with coreboot developers!!! (Thanks Nico Huber/@icon for the fix to fbwhiptail, efifb trampoline/exposition to kernel and imagemagick programmatically doing needed voodoo to have bootsplash and efifb today! See added patches under that PR for more details).
- Replaces i915drmfb which was previously driving graphics to a much simpler efifb kernel driver, which coreboot enables correctly (gain of 500kb firmware space)
- Makes fbwhiptail snappier! Refreshes barely noticible.
- Qemu/KVM targets now using same graphic init path, also permitting to boot into VESAFB enabled OSes, incluging tinycore a lot of people wanted for testing.
- No more flickering/screen corruption at kexec!
- No more hack needed under kexec to boot into next kernel.
The reason I need this PR to be merged is because of the 500kb freed space, and because this is a massive change that cannot be tested without boards owners testing new boot path. That is, most of the boards are affected by this change and it changes the way we use both the linux kernel and coreboot to boot our platforms from the graphic initialization routine up to how we kexec into the final OS kernel.
To whom I talked personally before, this permits to kexec into PureTinyCore, which was not working prior. Why? Because PureTinyCore, as the future of linux distributions trying to deprecate Legacy boot, PureTinyCore was only providing VESA framebuffer drivers. That is, it was impossible to boot into those OSes that were only providing VESA drivers into their initrd.
Fedora 36+ tried to deprecate Legacy boot before. And they are still planning to. This change in Heads makes it more resilient to the current planning, since it piggybacks into coreboot native graphic initialization to prepare a EFI compatible framebuffer (which can be initialized by GOP, Optional video rom or libgfxinit currently) and permits to use EFIFB provided by linux kernel by default. It is also compatible with simplefb and simpledrm on kexec’ed OS, so we do not care about the deprecation plan of VESA/higher DRM drivers into initrd and unified kernels anymore from the Heads side.
The PR to be tested this time, and the boards not currently have test reports is in the main post at libgfxinit/nativegfx init: efifb enforced fb (+coreboot ramstage enabled bootsplash) by tlaurion · Pull Request #1403 · osresearch/heads · GitHub
Instructions to test PR is at the current bottom post at libgfxinit/nativegfx init: efifb enforced fb (+coreboot ramstage enabled bootsplash) by tlaurion · Pull Request #1403 · osresearch/heads · GitHub
If you would be willing to be a recurrent tester of Heads, please notify me @tlaurion under Platform blobs, collaborators/maintainers/testers for faster problems resolution · Issue #692 · osresearch/heads · GitHub
Stay tuned for massive features coming soon! (Which will need less drastic testing then now, but still!!! Each time there is a coreboot/linux version bump or a change that is board specific, we need testers. So the more official willing testers we have, the faster testing occurs and the richer Heads will become!
Note on recent changes under Heads:
- Purism/Heads is now feature similar, thanks to the massive upstreaming effort and collaboration that happened recently with Purism:
Thank you all! Next step is Add secure thumb drive creation premisses by tlaurion · Pull Request #1446 · osresearch/heads · GitHub going toward risk-free Authentication under Heads (preventing unauthenticated: recovery shell access, flashing, unsafe boot or USB boot options).