You best do some reading about the basics then: e.g. What is a disk/SSD partition (wiki). LUKS is a container based either on a file, or, in your case, an SSD partition. The lsblk command categorically cannot list LUKS keyslots, but it can list partitions, among other things. Use the man utility to read about what commands do, e.g. man lsblk.
Okay I will
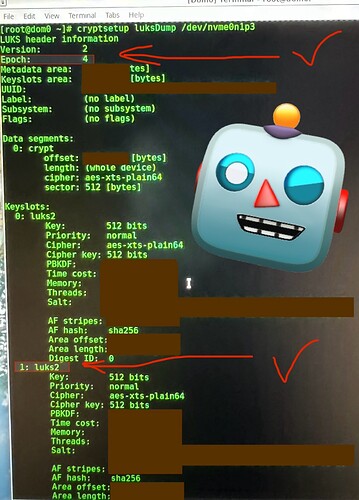
I am just concerned now, now knowing there was NO mention from Star Labs about a MasterKey as if they purposely don’t tell lay users this, the irony is advanced users would likely never have Qubes pre-installed anyway so this feels like ignorant and/or newbie users are being taken advantage of. Thus, since I realize there is also a MasterKey that is why I now have questions about what is going on with the KeySlots 0, 1, and 2 (specifically KeySlot 0). KeySlot 0 is not behaving like any of the others at all. I am just concerned now that’s all
But yes I will read up on what you gave me
But I also just need to do all this ASAP as the 1st of the Month approaches and I really need to get back online fully soon with a computer (this computer)
Skimmed over the Wiki
Still wondering,
Why would access be denied for KeySlot 0 then?
It doesn’t even let me try to enter a password, just returns with “does not exist or access denied” and I think it is “access denied” because if it didn’t exist then it would do what KeySlots 1 & 2 returned which was, “not a valid LUKS device”
Unless I am assuming wrong about what LUKS 1 & 2 output returns mean
Also applies here:
At this point I am just awaiting a follow-up reply response from @sm95
![]()
I have now added a 2nd Key Slot
using this CLI command while in ROOT
cryptsetup luksAddKey /dev/nvme0n1p3
I see it worked here as there is a new “1: luks2” added along with a new “Salt”
Also, I noticed the “Epoch” changed from 3 to 4
Now I need to run the CLI command to delete the “starlabs” login default Key Slot
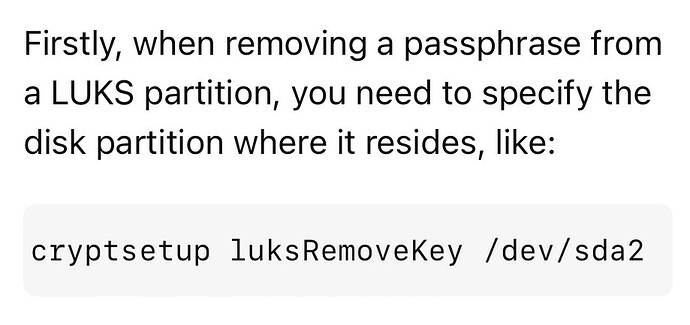
In an email from Star Labs they said to use this,
cryptsetup luksRemoveKey /dev/nvme0n1p3
BUT
I am worried
how does THAT command know which Key Slot to remove? Will it prompt me to pick/choose?
What if I run this CLI command and it deletes ALL the Key Slots in “nvme0n1p3”
I am so worried …
Can someone confirm this is the correct CLI command?
cryptsetup luksRemoveKey /dev/nvme0n1p3
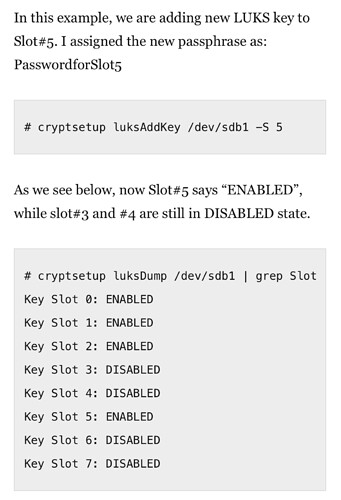
I found this:
source
So does this mean somewhere in the CLI command I have to tell it to specifically remove “0: luks2”?
How would I even do that specification?
Also, in that same thread they claim it isn’t truly deleted. Thus, now that I confirmed the new one worked I might should first Change the “0: luks2” and after changing THEN remove it, right?
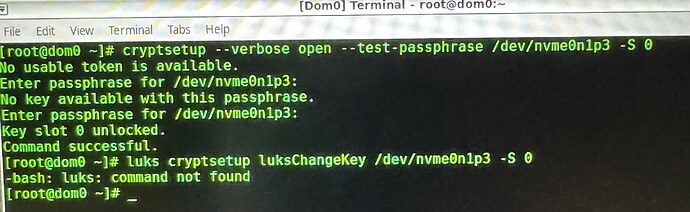
I think the command to change a KeySlot is:
luks cryptsetup luksChangeKey /dev/nvme0n1p3
BUT
again,
how to inert the specific command to tell it WHICH Key Slot to make sure I am now only alternating the oldest Key Slot the “0: luks2” and NOT the new “1: luks2”
I cant help you here because I have no idea what you are trying to do
with that image.
Also, posting images is easy for you - it’s of no help to someone who
might have exactly the same issue as you, but cant find this.
Search engines cant yet get text from images - you can.
I’ve already suggested you search for guides to this stuff - there’s
nothing Qubes specific here.
Also, you can get a good deal of help by using man - man cryptsetup
I got it here is my proof yay!
-
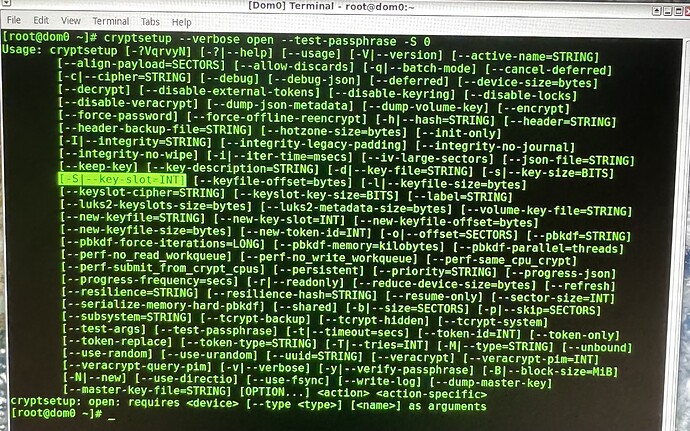
I wanted to know the command to specify a selected slot that seems to be
-S [insert number slot here] -
I needed to try it before deleting/removing that slot
-
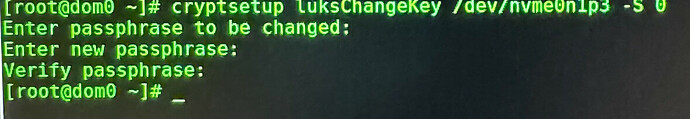
So I figured to change the passphrase for that specific Slot first to test the “-S” command
-
I read a rumor that removing it still doesn’t delete it so IMHO wouldn’t it be best to change the passphrase of the slot then prior to “removing” it to be extra thorough? So I did that
-
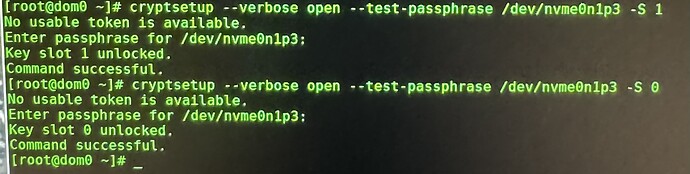
Now I hope to try to “remove” it without removing my new one by accident, accomplishing this hopefully via the “-S” CLI command
![]()
Hope that clarifies what I am attempting to accomplish here still following the advice that @sm95 gave above but with a few more added steps to be extra sure of everything
How do I insert “alt text” for accessibility and searches in my images for this Forum???
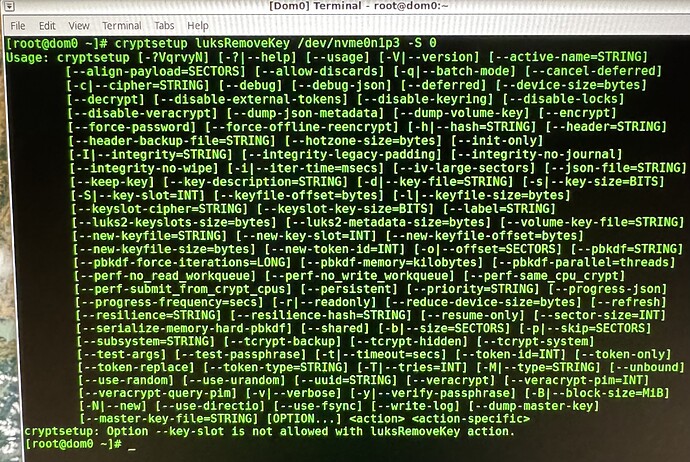
Return output states that “-S” slot designation CLI command cannot be used along side the “LUKS remove Key” action
![]()
Okay then how will I tell the computer exactly which KeySlot to remove
I fear if I merely input,
cryptsetup luksRemoveKey /dev/nvme0n1p3
It might remove all of them
or no?
Will it prompt me to choose which to remove?
I don’t want to find out the hard way … please someone let me know if this is safe
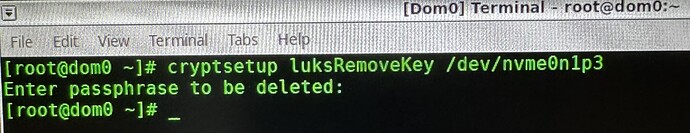
Alright!
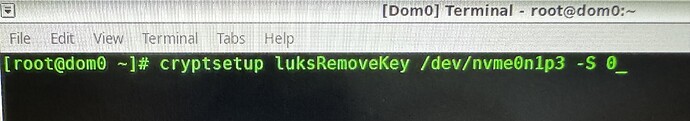
I took a chance …
THAT worked, as it lets the user define which key to be removed by prompting for the passphrase for the key being removed
whew, scary … but this part is now done.
Moving on, hope not to ruin my entire system by following directions now for the FDE passphrase change
![]()
eek
Any guidance to make extra sure the CLI commands for changing the Masterkey FDE as @sm95 gave directions on would be deeply appreciated
![]()
I am now moving onto that scary step
(it is scary for a me as a n00b)
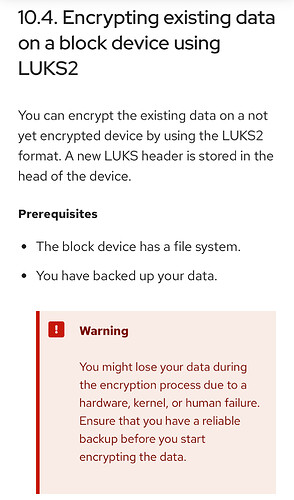
Does this mean once encrypted, there is no going back?
source
You must start over, to be able to reformat?
In other words no matter how careful I am in inputing a CLI command(s) for this, it will inevitably destroy the current data making me start over with a fresh install of QubesOS?