Here a how to:
Since this operation touches a very sensitive – core – part of your Qubes OS it is highly recommended to:
A) do a backup before continue with the procedure below and
B) do not rush through the steps you can logout yourself from your system.
This description is made for beginners. If you know what to do and you already know your LUKS partition you can do the password change with two command lines.
1.0. Make a Qubes Backup
Click on the “Q” application icon > System tools > Backup Qubes
2.0. Looking for the LUKS partition
Launch the dom0 terminal
Click on the “Q” application icon > Terminal Emulator
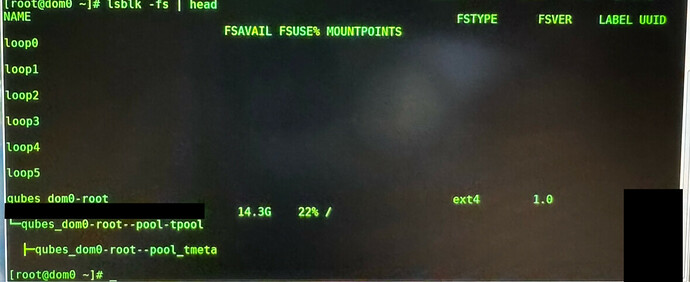
Command the following and check the output:
lsblk –fs | head
In the column FSTYPE it should be named crypto_LUKS, this points you to the corresponding NAME (first column) in my case it is sda2. In your case it can be different so please be careful and do not blindly copy & paste the following commands.
2.1. LUKS disk encryption has 8 “key slots” for your secrets (passwords or key files). Here we will touch passwords only. With the next command you can do both
A) check, which of them are used and
B) verify that you have selected the right LUKS partition.
sudo cryptsetup luksDump /dev/sda2 | grep Key.Slot
The terminal should return this (if you have set just one LUKS password; should be your default setting):
Key Slot 0: ENABLED
Key Slot 1: DISABLED
Key Slot 2: DISABLED
Key Slot 3: DISABLED
Key Slot 4: DISABLED
Key Slot 5: DISABLED
Key Slot 6: DISABLED
Key Slot 7: DISABLED
Key Slot 8: DISABLED
Note: If you have selected a wrong partition you will get this message:
Device dev/sdaX is not a valid LUKS device.
3.0. Modify LUKS password settings
You can add, change or delete LUKS keys. Not the quickest but safest way to change your password is the following.
3.1. Add a new password with:
sudo cryptsetup luksAddKey /dev/sda2
First, you will be asked to enter the old (current) password and afterwards you will be asked to enter your new password. It will store your new password on next free Key Slot.
Double check again the LUKS Key Slots (see 2.1) and verify that you have now 2 Key Slots ENABLED. In my case the Key Slot 0 contains the old password and the Key Slot 1 contains the new password.
3.2. Remove the old passwords
sudo cryptsetup luksRemoveKey dev/sda2
Now, you have to enter your old (previous) password it will automatically delete the corresponding Key Slot. Thus, Key Slot 0 is DISABLED and Key Slot 1 is set to ENABLED now.
4.0 Reboot your system and verify that your new LUKS password has been updated properly.
Done. 
Want more LUKS?

 )
)